a vulnerability in Amazon’s U.S. website attackers have the opportunity insert malicious code into the metadata of a Kindle e-books. You can gain access to user accounts thus.
The German security researcher Benjamin Mussler According includes Amazon’s Kindle library a cross-site scripting vulnerability (XSS ), through which an attacker can gain complete access to an Amazon.com account. Mussler has also published on his blog a feasibility exploit.
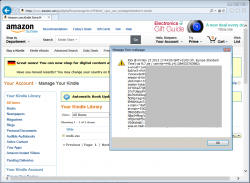
The Kindle library on Amazon.com has an XSS hole on (Image: Benjamin Mussler).
Mussler According attacker can inject malicious code into the metadata of a Kindle e-books, such as the title, paste, which is executed automatically, Shobal the victim’s Kindle Library page (also known as “Content and Device Management” or “Manage Kindle”) opens on Amazon.com. “In this way, Amazon account cookies can be accessed and transferred to the attacker and compromised the Amazon account of the victim,” Mussler.
explained according to the security researchers are fundamentally all the users affected, the Amazons use Kindle library to store e-books or to transfer them to their Kindle. Particularly vulnerable users who receive their e-books from untrusted sources were instead to buy directly from Amazon.
Mussler reported the gap claims to be the first time in November 2013 Amazon confidential. She was then closed relatively quickly. But with a later update its Web application “Manage Kindle” Amazon have introduced the bug accidentally again.
“Amazon did not respond to my following e-mail in which I explained the error, and two months later, the vulnerability is still not resolved, “said Mussler. Why he has now decided to publish the vulnerability
[with material from Björn Greif, ZDNet.de]
Tip:. How confident are you in safety? Check your knowledge – with 15 questions on silicon.de
![]()
No comments:
Post a Comment